BCS for SAP
Secure your SAP systems and applications against cyber threats with a powerful and dedicated security management solution.
Effectively detect, manage, and respond to unauthorized access, violations, fraud attempts, IP theft, and operational degradations threatening the compliance, stability, and security of your SAP systems.

Why BCS for SAP?

Integrate with your current security stack and onboard your SAP into Logpoint SIEM for heightened security robustness and improved threat detection. Strengthen your monitoring capabilities and detect threats earlier and faster before they impact your business.

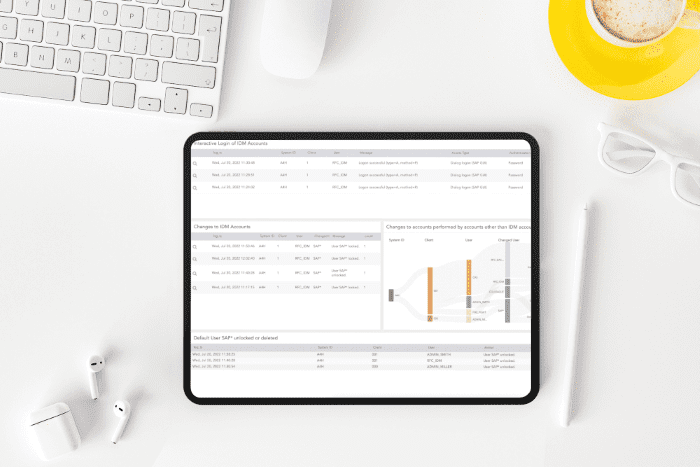
With end-to-end visibility throughout your entire infrastructure, you get an unparalleled view of your SAP system. Detect, analyze, and prioritize security incidents with predefined use cases, alert rules, and dashboards effectively.
Uncover advanced threats with out-of-the-box analytics. Detect suspicious transactions, deviations from standard business processes, and behavioral anomalies of SAP users. Successfully combat threats in the early stages of an attack.
SOLUTIONS:
Security and Audit Compliance Monitoring
64% of SAP systems have been breached during the past 24 months
SAP security is disconnected from the central security strategy. This hampers the ability to efficiently monitor, analyze and spot malicious activity. A security gap like this leaves businesses and organizations more exposed and vulnerable to attacks.


SOLUTIONS:
Business Integrity Monitoring
Quick detection is vital. Insider threats have risen by 44% over the past two years, costing $15.38 million per incident.
Detect and respond to the early signs of fraud before it impacts your revenue and compromises the integrity of your business. We help you uncover potential fraud patterns, so you can take the necessary steps to mitigate fraud risks.
SOLUTIONS:
Personal Identifiable Information (PII)
Can you afford to lose control of your sensitive assets? Inability to comply with regulations imposes fines of up to 4% of the annual turnover.
Knowing where your sensitive data resides, who has access to it, and how it’s monitored is almost an impossible task in a complex system comprising a multitude of applications and integrations.
Don’t operate in the dark! To pass SAP audits, you must meet compliance regulations such as GDPR, NIS2, and CCPA.


SOLUTIONS:
IT Service Intelligence
Outages are expensive – 1 in 3 costs over $1 million. Yet, during the past three years, 75% of all businesses have suffered from an outage.
Identify operational degradations across your entire SAP system early – before it impacts your business processes, internal teams and ultimately, your customers.
Ensure smooth operations, eliminate downtime, and avoid costly outages with complete insight across your landscape.
Want to know more about Logpoint?
Get a demo that is tailored to your needs
Let us show you around, hear more about your needs and requirements, and discuss how Logpoint can add value to your organization.
Our sales team will contact you shortly to discover your needs. Then our experts will run you through a customized demo and discuss how Logpoint can support you.
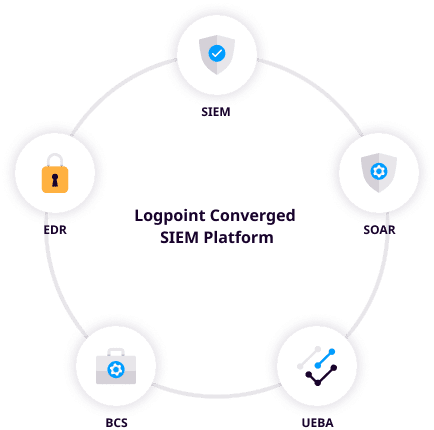
Converged SIEM
You can monitor your SAP systems and applications in one consolidated tech stack. See how BCS for SAP fits with SIEM, SOAR, UEBA, and Endpoint security. Converged SIEM helps SOC teams combine data sets from multiple sources. Instead of using multiple standalone products, they now have one single source of truth. It is the only unified platform that delivers SIEM+SOAR, UEBA, EDR capabilities and security monitoring of SAP for both enterprises and MSSPs.
- Full data integration for automated TDIR
- No integration or maintenance required
- Out-of-the-box compliance support
- Flexible deployment based on your needs